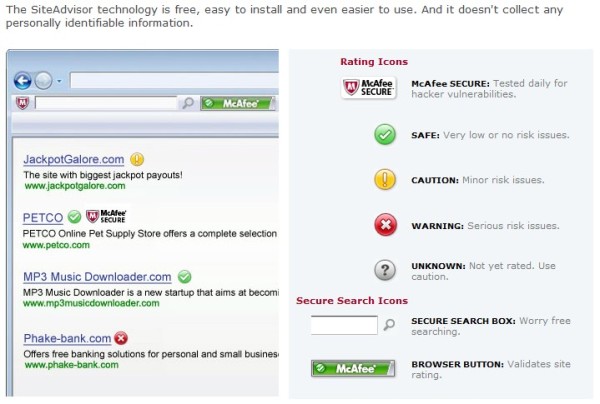
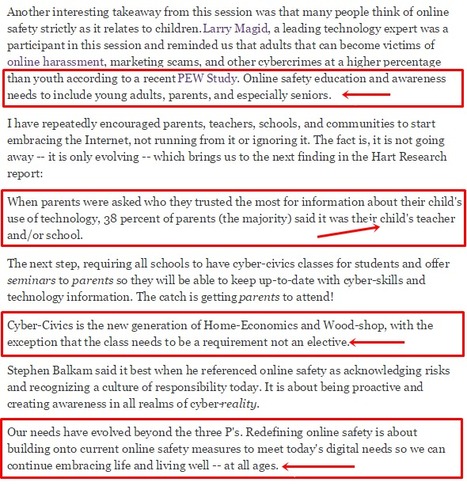
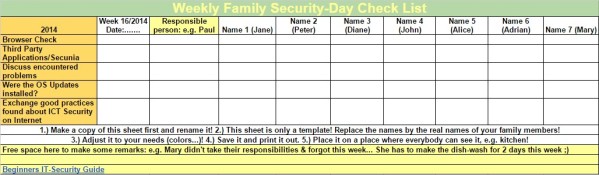
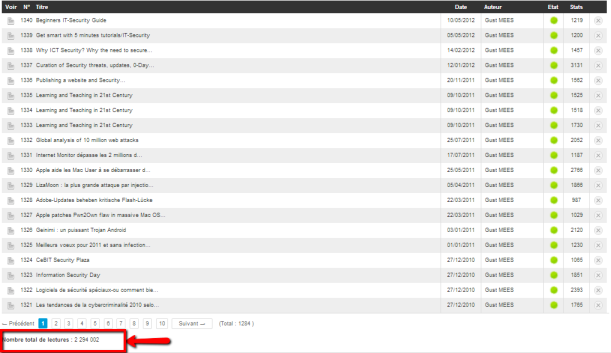
.
Image credit: http://www.ogilviedesign.co.uk/www.ogilviedesign.co.uk/Welcome.html
.
Safer Internet Day 2016 – Save the date!
.

.
.
Safer Internet Day (SID) is organised by Insafe in February of each year to promote safer and more responsible use of online technology and mobile phones, especially among children and young people across the world.
Safer Internet Day 2016 will be celebrated on Tuesday 09 February 2016, with the strapline of ===> “Play your part for a better internet” <=== following the success of last year’s campaign.
This website showcases some of the exciting activities and events that took place to celebrate the day in 2014. Click on the map below to get started, using the zoom control to locate the contacts and events in your country or visit the ‘SID Near You‘ section to explore news from the many countries and institutions involved. Visit the ‘SID Gallery‘ to find great resources from across the Insafe network and beyond to help you teach eSafety all year through.
For further information, read the summary or the full public report on Safer Internet Day 2014 activities and successes.
Keep checking back for the latest news as the SID 2016 starts to take shape.
.
.
Click the above image to access the article, please.
.
Check the video below, please, who explains about it.
.
.
.
.
My participation for the SID2016
 WHAT is special this year with my participation on SID2016?
WHAT is special this year with my participation on SID2016?
I created a ===> #GlobalCollaboration #blog <=== from @knolinfos (my pseudo on twitter) & @ICTPHMS & @kimmindy7 for #LEARNing about #DigitalCitizenShip. The authors are from Luxembourg/Europe (me), one female teacher from the USA and a male teacher from the USA WHO are using my blog post to learn together and sharing THEIR practice with YOU dear readers.
Well, there is a lot of different views about ===> Digital CitizenShip <=== WE will explore WHAT could be THE BEST way to teach and to learn about Digital CitizenShip (hashtag on Twitter is #digcit).
Here below the links of OUR blog post:
- Learning To Become a GOOD Digital Citizen | Digital CitizenShip (A Global-Collaboration Blog)
- PracTICE: Learning To Learn-Digital CitizenShip (A Global-Collaboration Blog)
How does it come that I post Global-Collaboration blog posts? Well, once the #ProfessionalDevelopment is Upto-Date, one does understand THAT learning in a team brings out a win-win situation and that a generation exchange is benefit for all of the participants as anyone learns from each other. BTW: here below other Global-Collaboration blogs with teaching persons from Australia, USA, France, Luxembourg (me):
- https://gustmees.wordpress.com/2014/07/10/education-collaboration-and-coaching-the-future/
- https://globaleducationandsocialmedia.wordpress.com/
.
My publications in the local press (Luxembourg/Europe) and interviews:
- https://gustmees.wordpress.com/2014/03/17/my-published-articles-about-cyber-security-in-the-press-and-social-media/
- https://dougpete.wordpress.com/2013/03/12/an-interview-with-gust-mees/
- https://gustmees.wordpress.com/2013/04/22/i-got-interviewed-feeling-honored/
.
This year I participate ALSO with blogs in three languages, in English, German and French.
.
I participate on #SID2016 in Luxembourg/Europe.
.
.Click the image above, please, to access the article.
.
Why should ===> anyone <=== participate?
.
========> Cyber-security – a shared responsibility <=======
.
Cyber-Security is a shared responsibility, WE are ALL responsible for a more secure Internet and it is ===> OUR responsibility to build up the future for OUR kids, learners and students! <===
WE can do it by learning and teaching the basics of Cyber-Security and ALSO by helping international organizations such as “Safer Internet Day” to become a catalyst for such a difficult task!!!
.
======> WE are living in a world of connected technology, Cyber-Security is a MUST!!! <======
.
.
That is why I am participating on SID2016 with my FREE courses here:
My English contributions:
-
Learning To Become a GOOD Digital Citizen | Digital CitizenShip (A Global-Collaboration Blog)
- PracTICE: Learning To Learn-Digital CitizenShip (A Global-Collaboration Blog)
- Digital CitizenShip: Social Media AND Privacy
-
WHY CyberSecurity STARTS At Home AND Is Concerning ALL Of Us
-
How To Teach Kids Up From The Early Age About Cyber Security And Digital CitizenShip
-
How To Teach Kids Up From The Early Age About Cyber Security And Digital CitizenShip
-
Digital CitizenShip | Internet Safety And Cyber Security Advisory Board Run by Students
- We are living in a world of connected technology – Cyber-Security knowledge is a MUST
- Authors, bloggers Toolbox for writing and sharing
- Not ONLY rights but also responsibility!?
- Are WE Becoming Too Paranoid About Cyber-Security?
- I Have Installed An Anti-Virus And A Firewall, Am I Protected NOW!?
- Digital Citizenship And ALSO Its Terminology
- Is My Professional Development Up-To-Date?
- Why (And How) Teachers and Education Should Start Learning and Teaching Cyber-Security
- Cyber-Security PracTICE: Verify Your Anti-Malware Solutions!
- Visual Cyber-Security: See Attacks On Real Time
-
Cyber-Security: The Weakest Link In The Security Chain Is The Human
- Learning basics of Cyber-Security
- Naivety in the Digital Age?
- Ideas for a more secure Internet-part2/IT-Security Scouts
- Why IT Security? Why the need to secure a computer?
- Beginners IT-Security Guide
- PC Security-HowTo Secure my PC
- PC Security-HowTo Fight Spam efficiently
- https://gustmeesen.wordpress.com/
- …
.
My German contributions:
.
My French contributions:
.
and also with my curation here:
- http://www.scoop.it/t/cyberbullying-it-s-not-a-game-it-s-your-life
- http://www.scoop.it/t/ict-security-tools
- http://www.scoop.it/t/securite-pc-et-internet
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
.
Motivation To Work Together, Give It A Try
 MOTIVATION: Knowing NOW how important it is to take part of such a great Event, I encourage YOU ALL to take part of it by any possible action, even as a private person! I encourage especially private persons to display the banner from SID2015 on their blogs and/or websites
MOTIVATION: Knowing NOW how important it is to take part of such a great Event, I encourage YOU ALL to take part of it by any possible action, even as a private person! I encourage especially private persons to display the banner from SID2015 on their blogs and/or websites ![]()
Where can I get the banners?
- Luxembourg (Europe):
- https://www.bee-secure.lu/de/tools/eu-events/safer-internet-day/safer-internet-day-2015 (Check on the bottom of the website)
- Worldwide
People who are on Twitter may use the hashtag #SID2016 to promote that Event, thanks for Helping to make the Internet a more secure place!
.
|
The author Gust MEES is ICT Course Instructor, ”Member of the Advisory Board” from “Luxembourg Safer Internet” (LuSI), BEESECURE, Official Partner (Consultant) from the Ministry of Education in Luxembourg, project “MySecureIT“, Official Partner from the Ministry of Commerce in Luxembourg, project “CASES” (Cyberworld Awareness and Security Enhancement Structure). |
.
|
. The author Dan KIRSCH teaches courses in Information/Communications & Technology (ICT) and Career/Technical Education (CTE) for students in grades 6-8 at Patrick Henry Middle School in South Dakota, USA. Students in his classes focus on Social Media, Educational Technology, and most importantly Digital Citizenship. . You can find me also on:
|
.
.
Stay tuned for next blog post(s) 😉
.
















 I will divide the tasks through a whole week, so it will be very easy for you to find the necessary time to achieve them, those who have the necessary time can, of course, achieve more tasks…
I will divide the tasks through a whole week, so it will be very easy for you to find the necessary time to achieve them, those who have the necessary time can, of course, achieve more tasks…